CVE-2025-5777
Citrix NetScaler ADC and Gateway Out-of-Bounds Read Vulnerability - [Actively Exploited]
Description
Insufficient input validation leading to memory overread when the NetScaler is configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) OR AAA virtual server
INFO
Published Date :
June 17, 2025, 1:15 p.m.
Last Modified :
Oct. 30, 2025, 8:10 p.m.
Remotely Exploit :
Yes !
Source :
[email protected]
CISA KEV (Known Exploited Vulnerabilities)
For the benefit of the cybersecurity community and network defenders—and to help every organization better manage vulnerabilities and keep pace with threat activity—CISA maintains the authoritative source of vulnerabilities that have been exploited in the wild.
Citrix NetScaler ADC and Gateway contain an out-of-bounds read vulnerability due to insufficient input validation. This vulnerability can lead to memory overread when the NetScaler is configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) OR AAA virtual server.
Apply mitigations per vendor instructions, follow applicable BOD 22-01 guidance for cloud services, or discontinue use of the product if mitigations are unavailable.
https://support.citrix.com/support-home/kbsearch/article?articleNumber=CTX693420 ; https://nvd.nist.gov/vuln/detail/CVE-2025-5777
Affected Products
The following products are affected by CVE-2025-5777
vulnerability.
Even if cvefeed.io is aware of the exact versions of the
products
that
are
affected, the information is not represented in the table below.
CVSS Scores
| Score | Version | Severity | Vector | Exploitability Score | Impact Score | Source |
|---|---|---|---|---|---|---|
| CVSS 3.1 | HIGH | [email protected] | ||||
| CVSS 4.0 | CRITICAL | [email protected] |
Solution
- Apply the latest NetScaler updates from the vendor.
- Ensure secure configurations for Gateway and AAA virtual servers.
Public PoC/Exploit Available at Github
CVE-2025-5777 has a 43 public
PoC/Exploit available at Github.
Go to the Public Exploits tab to see the list.
References to Advisories, Solutions, and Tools
Here, you will find a curated list of external links that provide in-depth
information, practical solutions, and valuable tools related to
CVE-2025-5777.
CWE - Common Weakness Enumeration
While CVE identifies
specific instances of vulnerabilities, CWE categorizes the common flaws or
weaknesses that can lead to vulnerabilities. CVE-2025-5777 is
associated with the following CWEs:
Common Attack Pattern Enumeration and Classification (CAPEC)
Common Attack Pattern Enumeration and Classification
(CAPEC)
stores attack patterns, which are descriptions of the common attributes and
approaches employed by adversaries to exploit the CVE-2025-5777
weaknesses.
We scan GitHub repositories to detect new proof-of-concept exploits. Following list is a collection of public exploits and proof-of-concepts, which have been published on GitHub (sorted by the most recently updated).
Mirror of https://github.com/nomi-sec/PoC-in-GitHub
None
Python
placeholder for CitrixBleed 2.0 CVE-2025-5777
CVE-2025-20337
Exploit for CVE-2025-5777: Citrix NetScaler Memory Disclosure (CitrixBleed 2)
citrixbleed-2 citrixbleed2 exploit-development
Shell
None
None
Python
Update the old POC of CVE-2025-5777 Citrix NetScaler Memory leak
Python
None
Python
CitrixBleed 2 NetScaler honeypot logs
None
Python
PoC for CVE-2025-5777 – Auth Bypass and RCE in Trend Micro Apex Central
authentication-bypass cve-2025-5777 exploit infosec kali-linux python rce redteam trendmicro
Python
None
CVE-2025-5777
Python
An advanced, powerful, and easy-to-use tool designed to detect and exploit CVE-2025-5777 (CitrixBleed 2). This script not only identifies the vulnerability but also helps in demonstrating its impact by parsing human-readable information from the memory leak.
Python
Results are limited to the first 15 repositories due to potential performance issues.
The following list is the news that have been mention
CVE-2025-5777 vulnerability anywhere in the article.

-
The Cyber Express
The Cyber Express Weekly Roundup: Escalating Breaches, Regulatory Crackdowns, and Global Cybercrime Developments
As February 2026 progresses, this week’s The Cyber Express Weekly Roundup examines a series of cybersecurity incidents and enforcement actions spanning Europe, Africa, Australia, and the United States ... Read more

-
The Cyber Express
Illinois Man Charged in Massive Snapchat Hacking Scheme Targeting Hundreds of Women
The Snapchat hacking investigation involving an Illinois man accused of stealing and selling private images of hundreds of women is not just another cybercrime case, it is a reminder of how easily soc ... Read more

-
CybersecurityNews
Hackers Actively Scanning Citrix NetScaler Infrastructure to Discover Login Panels
Scanning Citrix NetScaler Login A large-scale reconnaissance campaign targeting Citrix ADC Gateway and NetScaler Gateway infrastructure was detected between January 28 and February 2, 2026, by the Gre ... Read more

-
The Cyber Express
Inside the 2026 Business Blast Radius: Dr. Amit Chaubey on Why Cyber Disruption Is Now a Sovereign Risk
In an exclusive interview with The Cyber Express, Dr. Amit Chaubey, Managing Director and Board Chair of Chakra-X, provides new insight into what he calls the “2026 Business Blast Radius”, a rapidly e ... Read more

-
CybersecurityNews
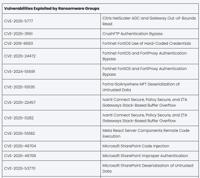
CISA Expands KEV Catalog with 1,484 New Vulnerabilities as Active Exploitation Surges 20% in 2025
The United States Cybersecurity and Infrastructure Security Agency (CISA) has significantly expanded its Known Exploited Vulnerabilities (KEV) Catalog to 1,484 vulnerabilities as of December 2025, mar ... Read more
-
The Cyber Express
CISA Known Exploited Vulnerabilities Soared 20% in 2025
After stabilizing in 2024, the growth of known exploited vulnerabilities accelerated in 2025. That was one conclusion from Cyble’s analysis of CISA’s Known Exploited Vulnerability (KEV) catalog data f ... Read more

-
Help Net Security
Cisco email security appliances rooted and backdoored via still unpatched zero-day
A suspected Chinese-nexus threat group has been compromising Cisco email security devices and planting backdoors and log-purging tools on them since at least late November 2025, Cisco Talos researcher ... Read more

-
CybersecurityNews
Top 20 Most Exploited Vulnerabilities of 2025: A Comprehensive Analysis
The cybersecurity landscape of 2025 has been marked by an unprecedented surge in vulnerability exploitation, with threat actors leveraging critical flaws across enterprise software, cloud infrastructu ... Read more

-
The Cyber Express
Password Manager LastPass Penalized £1.2m by ICO for Security Failures
The Information Commissioner’s Office (ICO) has fined password manager provider LastPass UK Ltd £1.2 million following a 2022 data breach that compromised the personal information of up to 1.6 million ... Read more

-
The Cyber Express
Barts Health Confirms Cl0p Ransomware Behind Data Breach Linked to Oracle Vulnerability
Barts Health NHS Trust has confirmed that the data breach at Barts Health was carried out by the Russian-speaking Cl0p ransomware group, which exploited a vulnerability in Oracle E-Business Suite. The ... Read more

-
The Cyber Express
Stolen VPN Credentials Most Common Ransomware Attack Vector
Compromised VPN credentials are the most common initial access vector for ransomware attacks, according to a new report. Nearly half of ransomware attacks in the third quarter abused compromised VPN c ... Read more

-
BleepingComputer
Pennsylvania AG confirms data breach after INC Ransom attack
The office of Pennsylvania's attorney general has confirmed that the ransomware gang behind an August 2025 cyberattack stole files containing personal and medical information. This comes after Attorne ... Read more

-
The Cyber Express
Android Reports Major Drop in Memory Bugs as Rust Adoption Accelerates
Android has shared new insights into how the platform’s long-term shift toward Rust is reshaping both security and software development. The new data reflects a decisive move toward memory safety, and ... Read more

-
The Cyber Express
Akira Ransomware Group Poses ‘Imminent Threat’ to Critical Infrastructure: CISA
The Akira ransomware group poses an “imminent threat to critical infrastructure,” the U.S. Cybersecurity and Infrastructure Security Agency (CISA) warned today. CISA joined with the FBI, other U.S. ag ... Read more
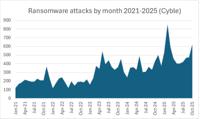
-
The Cyber Express
Ransomware Attacks Soared 30% in October
Ransomware attacks soared 30% in October to the second-highest total on record, Cyble reported today. The 623 ransomware attacks recorded in October were second only to February 2025’s record attacks, ... Read more

-
security.nl
Citrix Bleed en Cisco ISE-kwetsbaarheid als zero-day uitgebuit in geavanceerde aanvalscampagne
De Citrix Bleed 2 kwetsbaarheid (CVE-2025-5777) en een zero-day lek in een ongedocumenteerde endpoint van Cisco Identity Services Engine (ISE) (CVE-2025-20337) zijn door aanvallers uitgebuit voordat d ... Read more

-
The Cyber Express
Zero-Day Vulnerabilities in Cisco and Citrix Targeted by APT Group, Amazon Confirms
Amazon’s threat intelligence division has revealed a cyber-espionage campaign involving an advanced persistent threat (APT) group exploiting previously undisclosed zero-day vulnerabilities in systems ... Read more

-
The Register
Attackers turned Citrix, Cisco 0-day exploits into custom-malware hellscape
An "advanced" attacker exploited CitrixBleed 2 and a max-severity Cisco Identity Services Engine (ISE) bug as zero-days to deploy custom malware, according to Amazon Chief Information Security Officer ... Read more

-
CybersecurityNews
Hackers Actively Exploiting Cisco and Citrix 0-Days in the Wild to Deploy Webshell
An advanced hacking group is actively exploiting zero-day vulnerabilities in Cisco Identity Services Engine (ISE) and Citrix systems. These attacks, spotted in real-world operations, allow hackers to ... Read more

-
The Hacker News
Amazon Uncovers Attacks Exploited Cisco ISE and Citrix NetScaler as Zero-Day Flaws
Nov 12, 2025Ravie LakshmananNetwork Security / Zero-Day Amazon's threat intelligence team on Wednesday disclosed that it observed an advanced threat actor exploiting two then-zero-day security flaws ... Read more
The following table lists the changes that have been made to the
CVE-2025-5777 vulnerability over time.
Vulnerability history details can be useful for understanding the evolution of a vulnerability, and for identifying the most recent changes that may impact the vulnerability's severity, exploitability, or other characteristics.
-
Modified Analysis by [email protected]
Oct. 30, 2025
Action Type Old Value New Value Added Reference Type CISA-ADP: https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2025-5777 Types: US Government Resource Changed Reference Type CVE: https://citrixbleed.com Types: Third Party Advisory CVE: https://citrixbleed.com Types: Broken Link, Third Party Advisory -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Added Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2025-5777 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Removed Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2025-5777 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Added Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2025-5777 -
Modified Analysis by [email protected]
Aug. 14, 2025
Action Type Old Value New Value Added Reference Type CVE: https://citrixbleed.com Types: Third Party Advisory -
CVE Modified by af854a3a-2127-422b-91ae-364da2661108
Aug. 13, 2025
Action Type Old Value New Value Added Reference https://citrixbleed.com -
Modified Analysis by [email protected]
Jul. 14, 2025
Action Type Old Value New Value Added Reference Type CVE: https://horizon3.ai/attack-research/attack-blogs/cve-2025-5777-citrixbleed-2-write-up-maybe/ Types: Third Party Advisory Added Reference Type CVE: https://labs.watchtowr.com/how-much-more-must-we-bleed-citrix-netscaler-memory-disclosure-citrixbleed-2-cve-2025-5777/ Types: Third Party Advisory Added Reference Type CISA-ADP: https://reliaquest.com/blog/threat-spotlight-citrix-bleed-2-vulnerability-in-netscaler-adc-gateway-devices/ Types: Third Party Advisory Added Reference Type CVE: https://www.bleepingcomputer.com/news/security/cisa-tags-citrix-bleed-2-as-exploited-gives-agencies-a-day-to-patch/ Types: Press/Media Coverage, Third Party Advisory Added Reference Type CVE: https://www.netscaler.com/blog/news/netscaler-critical-security-updates-for-cve-2025-6543-and-cve-2025-5777/ Types: Third Party Advisory Added Reference Type CVE: https://www.theregister.com/2025/07/10/cisa_citrixbleed_kev/ Types: Press/Media Coverage -
CVE Modified by af854a3a-2127-422b-91ae-364da2661108
Jul. 12, 2025
Action Type Old Value New Value Added Reference https://horizon3.ai/attack-research/attack-blogs/cve-2025-5777-citrixbleed-2-write-up-maybe/ Added Reference https://labs.watchtowr.com/how-much-more-must-we-bleed-citrix-netscaler-memory-disclosure-citrixbleed-2-cve-2025-5777/ Added Reference https://www.bleepingcomputer.com/news/security/cisa-tags-citrix-bleed-2-as-exploited-gives-agencies-a-day-to-patch/ Added Reference https://www.netscaler.com/blog/news/netscaler-critical-security-updates-for-cve-2025-6543-and-cve-2025-5777/ Added Reference https://www.theregister.com/2025/07/10/cisa_citrixbleed_kev/ -
CVE CISA KEV Update by 9119a7d8-5eab-497f-8521-727c672e3725
Jul. 11, 2025
Action Type Old Value New Value Added Date Added 2025-07-10 Added Due Date 2025-07-11 Added Required Action Apply mitigations per vendor instructions, follow applicable BOD 22-01 guidance for cloud services, or discontinue use of the product if mitigations are unavailable. Added Vulnerability Name Citrix NetScaler ADC and Gateway Out-of-Bounds Read Vulnerability -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Jul. 10, 2025
Action Type Old Value New Value Added Reference https://reliaquest.com/blog/threat-spotlight-citrix-bleed-2-vulnerability-in-netscaler-adc-gateway-devices/ -
Initial Analysis by [email protected]
Jul. 10, 2025
Action Type Old Value New Value Added CVSS V3.1 AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N Added CWE CWE-908 Added CPE Configuration OR *cpe:2.3:a:citrix:netscaler_application_delivery_controller:*:*:*:*:-:*:*:* versions from (including) 13.1 up to (excluding) 13.1-58.32 *cpe:2.3:a:citrix:netscaler_application_delivery_controller:*:*:*:*:-:*:*:* versions from (including) 14.1 up to (excluding) 14.1-43.56 *cpe:2.3:a:citrix:netscaler_application_delivery_controller:*:*:*:*:fips:*:*:* versions from (including) 12.1 up to (excluding) 12.1-55.328 *cpe:2.3:a:citrix:netscaler_application_delivery_controller:*:*:*:*:fips:*:*:* versions from (including) 13.1 up to (excluding) 13.1-37.235 *cpe:2.3:a:citrix:netscaler_application_delivery_controller:*:*:*:*:ndcpp:*:*:* versions from (including) 13.1 up to (excluding) 13.1-37.235 *cpe:2.3:a:citrix:netscaler_gateway:*:*:*:*:*:*:*:* versions from (including) 13.1 up to (excluding) 13.1-58.32 *cpe:2.3:a:citrix:netscaler_gateway:*:*:*:*:*:*:*:* versions from (including) 14.1 up to (excluding) 14.1-43.56 Added Reference Type CISA-ADP: https://doublepulsar.com/citrixbleed-2-exploitation-started-mid-june-how-to-spot-it-f3106392aa71 Types: Third Party Advisory Added Reference Type Citrix Systems, Inc.: https://support.citrix.com/support-home/kbsearch/article?articleNumber=CTX693420 Types: Vendor Advisory -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Jul. 09, 2025
Action Type Old Value New Value Added CWE CWE-457 Added Reference https://doublepulsar.com/citrixbleed-2-exploitation-started-mid-june-how-to-spot-it-f3106392aa71 -
CVE Modified by [email protected]
Jun. 24, 2025
Action Type Old Value New Value Changed Description Insufficient input validation leading to memory overread on the NetScaler Management Interface NetScaler ADC and NetScaler Gateway Insufficient input validation leading to memory overread when the NetScaler is configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) OR AAA virtual server -
New CVE Received by [email protected]
Jun. 17, 2025
Action Type Old Value New Value Added Description Insufficient input validation leading to memory overread on the NetScaler Management Interface NetScaler ADC and NetScaler Gateway Added CVSS V4.0 AV:N/AC:L/AT:N/PR:N/UI:N/VC:H/VI:H/VA:H/SC:L/SI:L/SA:L/E:X/CR:X/IR:X/AR:X/MAV:X/MAC:X/MAT:X/MPR:X/MUI:X/MVC:X/MVI:X/MVA:X/MSC:X/MSI:X/MSA:X/S:X/AU:X/R:X/V:X/RE:X/U:X Added CWE CWE-125 Added Reference https://support.citrix.com/support-home/kbsearch/article?articleNumber=CTX693420


